The Definitive Guide to Zero Trust Security: Beyond the Hype to Modern Cyber Resilience
Introduction: The Death of the Traditional Perimeter
For decades, cybersecurity operated on a "castle-and-moat" principle: build strong walls (firewalls) around your network, and trust everyone inside. This model collapsed under the weight of cloud migration, remote work, and sophisticated threats. Enter Zero Trust Security—a paradigm shift from "trust but verify" to "never trust, always verify." By 2023, 61% of organizations had formal Zero Trust initiatives, up from 16% in 2018 1. This guide unpacks Zero Trust’s principles, evolution, implementation, and why it’s the future of cyber defense.
1. What is Zero Trust Security?
Zero Trust is a strategic framework that assumes all users, devices, and network traffic are potential threats. Unlike perimeter-based models, it enforces:
- Continuous verification of identity and device health.
- Least-privilege access (users get only the permissions they need).
- Microsegmentation to contain breaches 26.
As Microsoft succinctly states: "Never trust, always verify" 8.
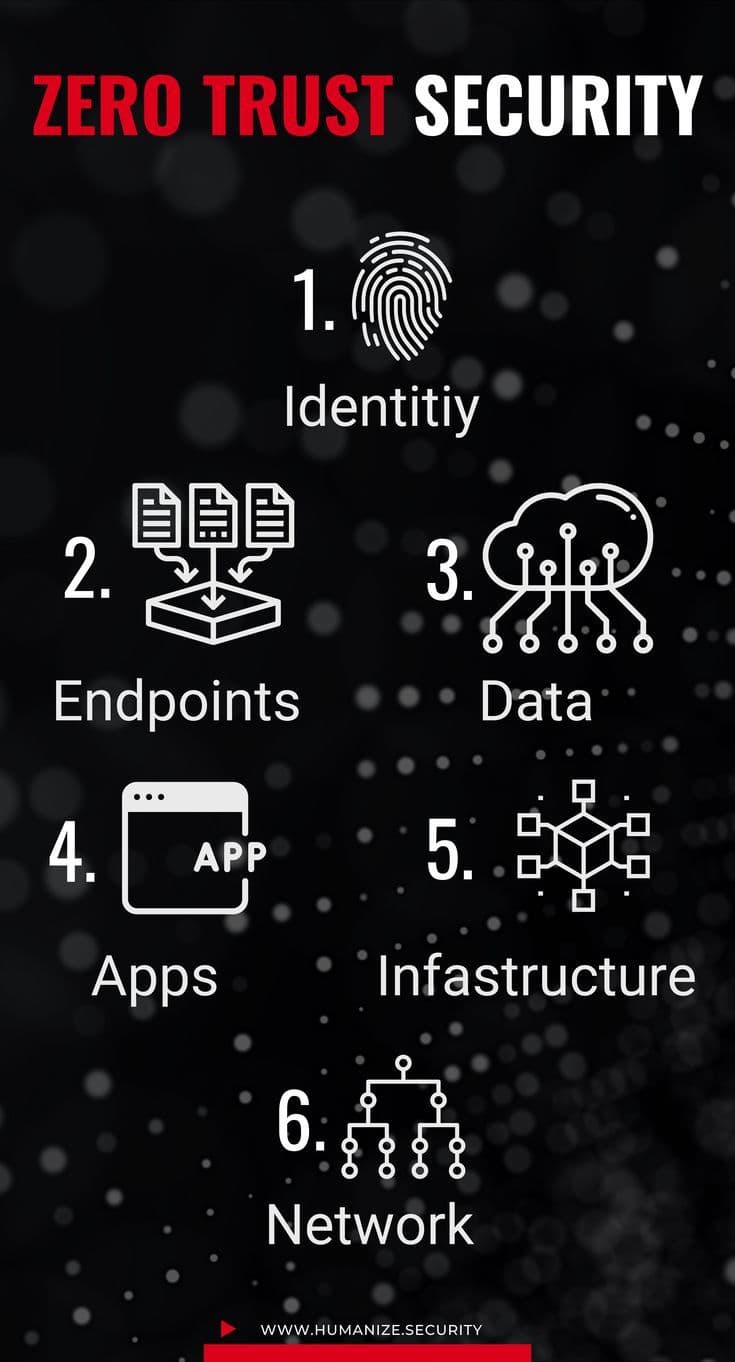
Key Components:
- Identity Verification: Multi-factor authentication (MFA) and strict access controls.
- Device Security: Continuous monitoring of endpoints (laptops, IoT devices).
- Data-Centric Protections: Encryption and access policies based on data sensitivity 410.
2. The Evolution: From "Black Core" to Mainstream
Zero Trust wasn’t born overnight. Key milestones include:
- 2004: Paul Simmonds proposed "de-perimeterization" as firewalls failed against worms like Blaster 1.
- 2009: Forrester’s John Kindervag coined "Zero Trust," emphasizing microsegmentation and least privilege 110.
- 2014: Google’s BeyondCorp proved Zero Trust at scale, ditching VPNs for internet-based access 1.
- 2020: NIST’s SP 800-207 standardized Zero Trust architecture, making it actionable 410.
Table: Traditional Security vs. Zero Trust
AspectTraditional ModelZero Trust ModelTrust BasisLocation (inside network)Continuous verificationAccess ControlBroad permissionsLeast privilegeBreach ResponseLimited containmentMicrosegmentationRemote WorkVPN-dependentLocation-agnostic
3. Core Principles of Zero Trust
A. Verify Explicitly
Every access request is authenticated using multiple data points: user identity, device health, location, and behavioral analytics. For example, a login from an unpatched device in a new country triggers MFA or denial 48.
B. Least Privilege Access
Users receive minimal permissions needed for their role. Just-In-Time (JIT) access grants temporary elevation for sensitive tasks. This limits damage from compromised credentials—61% of breaches involve stolen credentials 711.
C. Assume Breach
Operate as if threats are already inside your network. Tactics include:
- Microsegmentation: Splitting networks into isolated zones to halt lateral movement.
- End-to-end encryption: Protecting data in transit and at rest.
- Real-time analytics: Detecting anomalies like abnormal data downloads 48.
4. Implementing Zero Trust: A Step-by-Step Framework
Phase 1: Assess and Plan
- Map your "protect surface": Identify critical data, assets, and applications (DAAS) 6.
- Audit identities and devices: Inventory all users, endpoints, and permissions.
Phase 2: Deploy Foundational Controls
- Enforce MFA: Replace passwords with phishing-resistant methods (e.g., security keys) 25.
- Adopt Zero Trust Network Access (ZTNA): Replace VPNs with granular, app-specific access 26.
- Segment networks: Isolate high-value resources (e.g., financial databases) 4.
Phase 3: Automate and Optimize
- Integrate threat intelligence: Feed data from SIEM, EDR, and identity providers.
- Enable continuous monitoring: Use AI to analyze traffic patterns and flag deviations 412.
Table: Zero Trust Implementation Roadmap
StageKey ActionsTools/TechnologiesAssessIdentify critical assets; Audit permissionsIAM, Data classification toolsSecureDeploy MFA; Implement microsegmentationZTNA, Next-gen firewallsAutomateEnable real-time analytics; Enforce policiesSIEM, UEBA, SOAR platforms
5. Why Zero Trust? Tangible Benefits
- Reduce Breach Impact: Companies using Zero Trust contain attacks 50% faster, lowering average breach costs ($3 million+) 211.
- Enable Remote Work: Securely support hybrid teams without VPN bottlenecks.
- Meet Compliance: Aligns with GDPR, HIPAA, and U.S. Executive Order 14028 810.
- Simplify IT: Replaces patchwork security tools with unified policies 6.
6. Challenges and Pitfalls
Despite its promise, Zero Trust faces hurdles:
- Vendor Hype: 70% of "Zero Trust" products rebrand existing tools without true architecture 1.
- Complex Implementation: Legacy systems and unmanaged devices (e.g., IoT) complicate deployment 512.
- User Experience: Overzealous MFA prompts cause frustration. Balance security with usability 511.
Pro Tip: Start with high-risk areas (e.g., cloud admin accounts) before enterprise-wide rollout 11.
7. Real-World Success Stories
- Google BeyondCorp: Shifted 100,000+ employees to perimeter-less access. Results: Eliminated VPNs, reduced breaches, and enabled seamless remote work 1.
- U.S. Federal Government: Mandated Zero Trust by 2024 under EO 14028. Agencies like CISA use it to protect critical infrastructure 8.
- Financial Sector: Banks segment payment systems from employee networks, blocking ransomware spread 6.
8. The Future of Zero Trust
Zero Trust is evolving with:
- AI-Driven Policies: Adaptive access based on real-time risk scoring (e.g., flagging unusual data access).
- SASE Convergence: Integrating ZTNA with SD-WAN for secure edge networking 210.
- Passwordless Authentication: Phasing out credentials with biometrics and hardware tokens 11.
Conclusion: Zero Trust as a Strategic Imperative
Zero Trust isn’t a product—it’s a fundamental rethinking of security for the perimeter-less world. As cloud adoption and remote work accelerate, its principles offer the only viable defense against advanced threats. Implementation takes 2–3 years 11, but incremental steps (MFA, microsegmentation) yield immediate gains. Start now, or risk becoming another breach statistic.